Instagram For Windows Crack Disk
WELCOME is a home for the Call of Duty community and a hub for the discussion and sharing of content relevant to the game series. Call of Duty is a first-person shooter video game developed by Infinity Ward, Treyarch, and Sledgehammer Games, published by Activision.
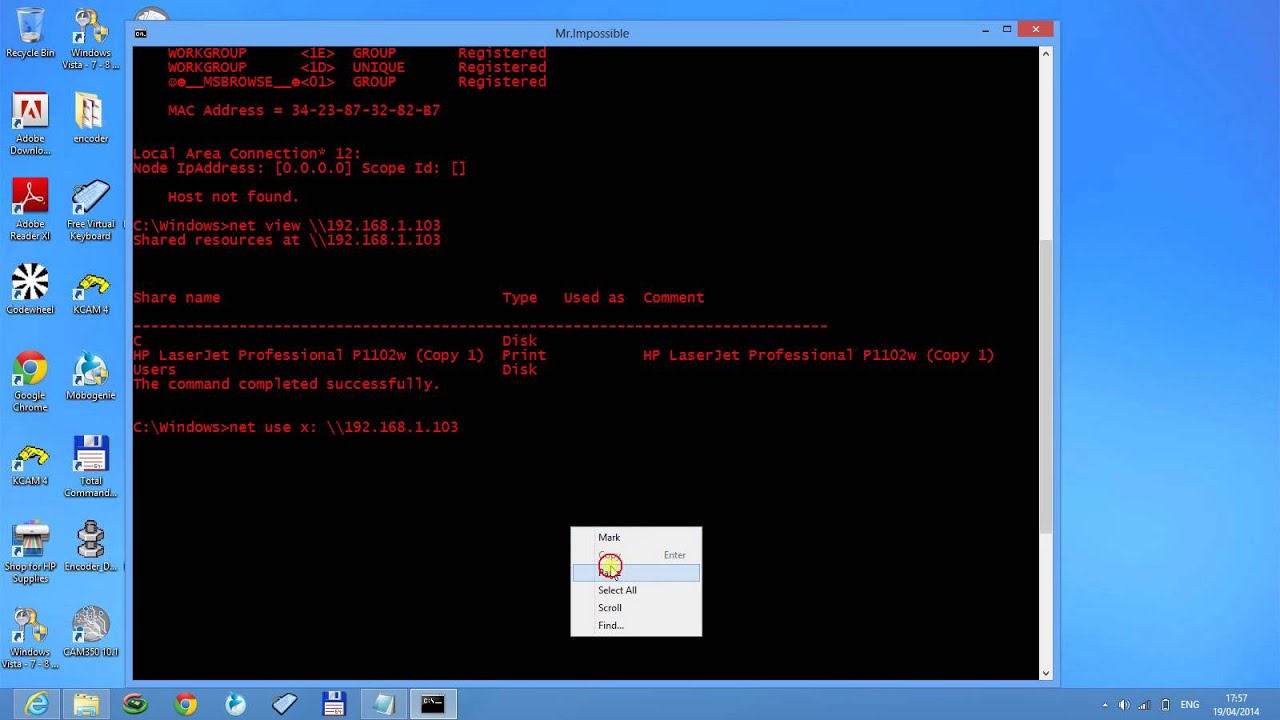
Once the disk is done booting, Ophcrack should start automatically and will begin cracking the passwords for all of the users on your computer. Note: If the computer boots and you only have a blank screen or Ophcrack doesn’t start, try restarting the computer and selecting manual or low RAM options on the live CD boot menu. System Update Readiness Tool for Windows 7 (32-bit) Free. Remove the inconsistency in the Windows servicing store which may prevent the successful installation of future updates, service packs, and software.
RULES For a more detailed explaination of these rules, please visit our. All Submissions should be relevant to Call of Duty.
No Derogatory Language, Harassment, Bullying, Witch Hunting, etc. No Low Quality Submissions. No Repetitive Topics / Reposts.
No Self-Promotion. No Party-Up or Clan/Team Recruitment. No Advertising, Selling, Buying, or Trading. Have fun, be nice. Moderators reserve the right to remove any content or user based off of their own discretion. Moderators will remove any post deemed to be detrimental to the subreddit.
I recently obtained a copy of the original Call of Duty, but my computer doesn't have a CD/DVD drive. Because of this, I had to come up with a solution. I could have just bought the game on Steam, but it still costs 20 bucks on there, and I wasn't willing to spend that much money on a game that came out shortly after I was born. Please note that I used the GOTY edition for this, and that this may work differently with other releases. What you need for this tutorial:. a copy of the original Call of Duty (you can find these on eBay for less than 5 bucks). the 1.5 patch, found.
the NoCD exe, found (this isn't optional, it only runs on Windows 10 with this exe). You have to click on the floppy disk icon to download. Step 1: Installing Call of Duty. First, you'll go on your computer with a CD drive to create.iso images of the CDs. If you have a Mac, Disk Utility doesn't work, so you'll have to copy the files on the CDs to a flash drive then use on Windows to create an ISO from the folder (tutorial ). This is the method I used.
However, if you have an old Windows PC with a disk drive, you can use IMGBurn to create an ISO directly from the CDs. With that done, you can now mount the ISO of the first CD. This built into Windows 8 and 10 (right-click, mount), but you can use or if you're on Windows 7. Now open the CD that should now show up as being in your 'CD drive' in My Computer, and open Setup.exe. It will ask you to input your CD key, which is on the back of the manual. It will install up to about 50%, then ask you to insert Disc 2. Eject the Disk 1 ISO by right-clicking on the icon in My Computer, then clicking on Eject, then mount the second one using the method previously described.
Then click OK in the installer. It should install the rest of the game, then ask you to reinsert Disc 1. Eject Disk 2 using the method previously described then mount Disk 1 again and press OK. If an error appears, DO NOT WORRY.
This is normal. Just press Abort, and if it asks you to roll back the previous changes, press no. The game should appear in the install directory, which is in C://Program Files (x86) by default. Step 2: Updating the game to the latest version. If when you launch the multiplayer.exe, it says 1.5 in the bottom right corner, you can safely skip this step.
If it says anything else (1.2, 1.3, 1.4, 1.1, etc), extract and install the patch linked above. It should find your install directory, but if it doesn't, browse and select it. After the update is installed, the installer will ask you if you want to install Xfire.
Just press no, there are very few servers still alive, so it's easy to find a friend, and there will probably be many problems trying to get Xfire to work, though I may be wrong. Step 3: Using the fixed.exe. NOTE: If you don't use this exe, singleplayer won't boot, even with the ISO mounted. With that said, just extract the codsp.exe file from the.rar file and copy and replace it with the original file in your install directory. The game should work fine now! I hope this tutorial will help us lonely few who play the original CoD, and please tell me if there are any mistakes in my tutorial that should be rectified.
It's not about you liking or disliking physical copies. It's mainly directed at other people who don't want to follow some lame ass bullshit to play a fucking game. Your solution relies on someone having multiple computers. A download cuts out the bullshit and is far more convenient that waiting for things to get shipped.
And if it's used, praying that it's not scratched to hell and back and still works. The alternative is to get a digital copy, which is why there are several responses stating such!
Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for and, and, and even online passwords using. Now, I thought it might be worthwhile to begin in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.
We will start with the basic principles of password cracking that are essential to ALL password cracking techniques, followed by some of the tools and technologies used. Then, one by one, I will show you how to use those principles and technologies effectively to crack or capture the various types of passwords out there.
The Importance & Methods of Password Cracking Passwords are the most widely used form of authentication throughout the world. A username and password are used on computer systems, bank accounts, ATMs, and more. The ability to crack passwords is an essential skill to both the hacker and the, the latter needing to hack passwords for accessing the suspect's system, hard drive, email account, etc. Although some passwords are very easy to crack, some are very difficult. In those cases, the hacker or forensic investigator can either employ greater computing resources (a botnet, supercomputer, GPU, ASIC, etc.), or they can look to obtain the password in other ways.
These ways might include insecure storage. In addition, sometimes you don't need a password to access password-protected resources. For instance, if you can replay a cookie, session ID, a Kerberos ticket, an authenticated session, or other resource that authenticates the user after the password authentication process, you can access the password protected resource without ever knowing the password. Sometimes these attacks can be much easier than cracking a complex and long password. I will do a tutorial on various replay attacks in the near future (look out specifically for my upcoming article on stealing the Facebook cookie to access someone's Facebook account). Now, let's start with the basics.
Step 1: Password Storage In general, passwords are not stored in clear text. As a rule, passwords are stored as hashes. Hashes are one-way encryption that are unique for a given input.
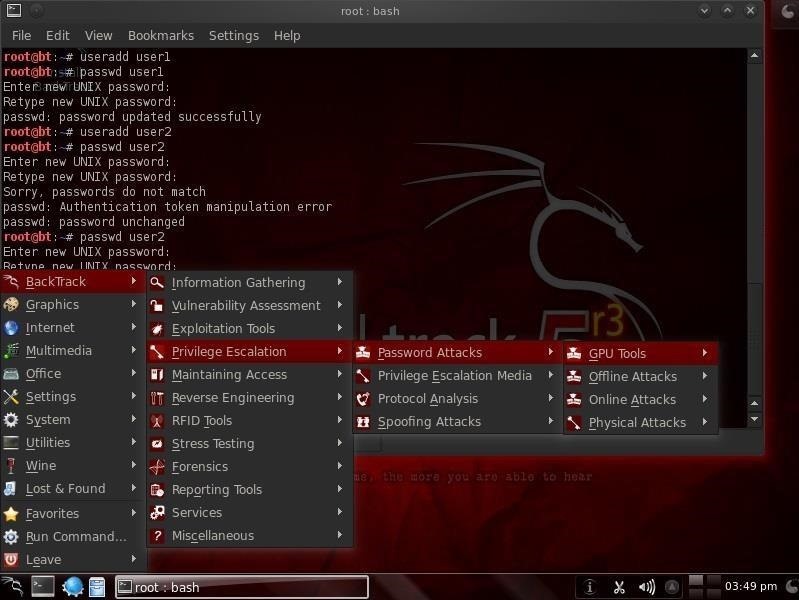
These systems very often use MD5 or SHA1 to hash the passwords. In the Windows operating system, passwords on the local system are stored in the SAM file, while Linux stores them in the /etc/shadow file. These files are accessible only by someone with root/sysadmin privileges. In both cases, you can use a service or file that has root/sysadmin privileges to grab the password file (e.g. DLL injection with samdump.dll in Windows).
Step 2: Types of Attacks Dictionary A dictionary attack is the simplest and fastest password cracking attack. To put it simply, it just runs through a dictionary of words trying each one of them to see if they work. Although such an approach would seem impractical to do manually, computers can do this very fast and run through millions of words in a few hours. This should usually be your first approach to attacking any password, and in some cases, it can prove successful in mere minutes. Rainbow Table Most modern systems now store passwords in a hash.
Crack Windows 10
This means that even if you can get to the area or file that stores the password, what you get is an encrypted password. One approach to cracking this encryption is to take dictionary file and hash each word and compare it to the hashed password. This is very time- and CPU-intensive. A faster approach is to take a table with all the words in the dictionary already hashed and compare the hash from the password file to your list of hashes. If there is a match, you now know the password. Brute Force Brute force is the most time consuming approach to password cracking.
It should always be your last resort. Brute force password cracking attempts all possibilities of all the letters, number, special characters that might be combined for a password and attempts them. As you might expect, the more computing horsepower you have, the more successful you will be with this approach. Hybrid A hybrid password attack is one that uses a combination of dictionary words with special characters, numbers, etc.
Often these hybrid attacks use a combination of dictionary words with numbers appending and prepending them, and replacing letters with numbers and special characters. For instance, a dictionary attack would look for the word 'password', but a hybrid attack might look for 'p@$$w0rd123'. Step 3: Commonly Used Passwords As much as we think each of us is unique, we do show some common patterns of behavior within our species. One of those patterns is the words we choose for passwords. There are number of wordlists that have been compiled of common passwords. In recent years, many systems have been cracked and passwords captured from millions of users.
By using these already captured passwords, you are likely to find at least a few on the network you are trying to hack. Step 4: Password Cracking Strategy Many newbies, when they start cracking passwords, simply choose a tool and word list and then turn them loose. They are often disappointed with the results.
Expert password crackers have a strategy. They don't expect to be able to crack every password, but with a well-developed strategy, they can crack most passwords in a very short amount of time. The key to develop a successful strategy of password cracking is to use multiple iterations, going after the easiest passwords with the first iteration to the most difficult passwords using different techniques for each iteration.
Step 5: Password Cracking Software John is probably the world's best known password cracking tool. It is strictly command line and strictly for Linux. Its lack of a GUI makes a bit more challenging to use, but it is also why it is such a fast password cracker. One of the beauties of this tool is its built in default password cracking strategy. First, attempts a dictionary attack and if that fails, it then attempts to use combined dictionary words, then tries a hybrid attack of dictionary words with special characters and numbers and only if all those fail will it resort to a brute force. Ophcrack Ophcrack is a free rainbow table-based password cracking tool for Windows. It is among the most popular Windows password cracking tools (Cain and Abel is probably the most popular; see below), but can also be used on Linux and Mac systems.
Password Crack Disk
Cain and Abel can crack passwords using a dictionary attack, rainbow attack, and brute force. One of its better features is the ability to select the password length and character set when attempting a brute force attack. And besides being an excellent password cracking tool, it is also a great and tool. THC-Hydra is probably the most widely used online hacking tool. It is capable of cracking web form authentication, and when used in conjunction with other tools such as Tamper Data, it can be a powerful and effective tool for cracking nearly every type of online password authentication mechanism. It is only available for Linux and requires a bit of a learning curve to master, but you will be richly rewarded for the time spent learning it. In addition, to be most effective you will need to use, so check their extensive list before buying your card.
You can find more info on aircrack-ng over in. Aircrack-ng is built into and and can be downloaded.
Step 6: Password Cracking Hardware Botnet Password cracking is simply a function of brute force computing power. What one machine can do in one hour, two machines can do in a half hour. This same principle applies to using a network machines. Imagine what you can do if you could access a network of one million machines!
Some of the botnets available around the globe are more than a million machines strong and are available for rent to crack passwords. If you have a password that might take one year to crack with your single CPU, a million-machine botnet can cut that time to approximately 1 millionth the time, or 30 seconds! GPU GPUs, or graphical processing units, are much more powerful and faster than CPU for rendering graphics on your computer and for cracking passwords. We have a few tools built into Kali that are specially designed for using GPUs to crack passwords, namely cudahashcat, oclhashcat, and pyrit.
Look for coming tutorials on using these tools and the GPU on your high-end video card to accelerate your password cracking. ASIC In recent years, some devices have been developed specifically for hardware cracking. These application-specific devices can crack passwords faster than over 100 CPUs working symmetrically. Master OTW, I just made an account on null-byte but i've been following your posts and tutorials for a while now. I must say they are excellent and i'm learning a lot! One thing i've been struggling with is to install the NVIDIA driver for my gt540m(oldie) so that i can use programs like pyrit and cudahashcat.